Authentication
is a process in which the credentials provided are compared to those
on file in a database of authorized users' information on a local
operating system or within an authentication server. If the
credentials match, the process is completed and the user is granted
authorization for access.
Encryption
is the most effective way to achieve data security. To read an
encrypted file, you must have access to a secret key or
password that enables you to decrypt it. Unencrypted data is called
plain text ; encrypted data is referred to as cipher text.
How to define digital payments?
Payments are made using
payment instruments. Cash, for example, is a payment instrument. So
too are checks. However, digital payments are not one instrument but
rather an umbrella term applied to a range of different instruments
used in different ways. In this section, we provide some parameters
for creating this definition.
Since there is no one
standard definition of a digital or e-payment, you should settle on a
clear and implementable definition at the start of any measurement
exercise. The subject matter is complex, but there are two key
dimensions of categorization that are most important:
- the nature of the payment instrument: through which means—paper or digital—are the instructions carried.
- the payer-payee interface: whether the payer, payee, or both use an electronic medium in a payment transaction.DEFINITION of 'Digital Money'
Any
means of payment that exists purely in electronic form. Digital money
is not tangible like a dollar bill or a coin. It is accounted for and
transferred using computers. Digital money is exchanged using
technologies such as smartphones, credit
cards and the internet. It can be turned into physical money by,
for example, withdrawing cash at an ATM.
BREAKING DOWN 'Digital Money'
Financial
services companies facilitate digital money transfers
and foster online transactions between complete strangers across long
distances. Without digital money, many online retail websites would
operate much less efficiently. Digital money also makes it possible
to bank online or via smartphone, eliminating the need to use cash or
to visit a bank in person.
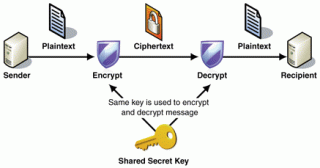
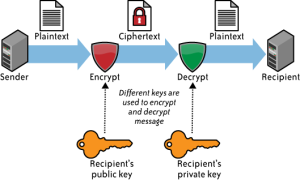
Symmetric and Asymmetric Algorithm
Symmetric
and Asymmetric Cryptography is a type of cryptographic algorithms
based on key usage. In short, symmetric cryptography uses the same
key to perform encryption and decryption while asymmetric
cryptography uses different keys to encrypt
and decrypt.
Examples of symmetric algorithm is AES, DES, RC4, etc. while the
asymmetric are RSA, ElGamal etc. Picture below is an encryption and
decryption process symmetric
and asymmetric
algorithms.
Symmetric
Asymmetric Algorithm
In
asymmetric algorithms, there are two keys that public key to encrypt
and the private key to decrypt.
When a person (eg Alice) sends a message to Bob, then Alice will
encrypt the message using the public key Bob and Bob will open a
received message using the
private
key. This is an advantage in asymmetric systems because sufficient
user store his private key secret, while the public key can be
distributed to all users who want to communicate with him without
worrying about unauthorized person can open the message using the
public key that has been deployed it.
In
symmetric
systems,
the key used to encrypt
and decrypt
are the same, so users who communicate with each other using
symmetric
system should be exchanging a common key because if they do not use
the same key, the message can not be open at the receiver side. If
there is someone who is in the process send thank tengah2 key and
managed to get the key then all the messages can be opened. Unlike
the asymmetric
system,
the user only needs to send a public key so that other people can
communicate with him. Users do not need to fear the attacker can
reconstruct the private
key
from the public key acquired.
The
complexity of the symmetric
key distribution higher than asymmetric.
Each one on a symmetric
key used by two users or a group to communicate. Me illustrate as
follows, when the user A will communicate with user B they use the
key X, and when the user A to communicate with the user C they would
use the keys Y. Then, when the user B, C, D will send a message to a
user A, user A will use 3 pieces of different keys to open a received
message. Unlike the asymmetric
system,
user B, C, D can simply use a public key to send messages and A
fairly use its private key to open the message.
However,
symmetric
systems faster in computing and the resulting ciphertext
less so as not to burden the bandwidth during the process of sending
messages. Usually symmetric and asymmetric
often used together in a system. For example in the video conference
system Agievic, asymmetric
used for symmetric
key distribution,
symmetric
key is used to encrypt communications for video conferencing.
Securing your email
There are several important steps you can take to improve the security of your email communications.
First, you must make sure that only the people you're emailing the one who can read the message.
This is discussed in the section fixed Keeping your webmail private and Switching to a more secure email account.
Sometimes it is important for the recipient to be able to verify that the received message actually came from you, instead of someone else posing as you.
One way to do it is described in the Email Security on the Advanced Encryption and authentication of individual email messages
You also need to know what to do if your confidentiality of your email uncovered.
Tips section responds to emails suspected email surveillance will answer these questions
Remember also that secure email will not be useful if what you type is recorded by spyware and periodically sent to third parties over the Internet.
Chapter 1: How to protect your computer from malware and hacker / hacker provides several ways to prevent such things, and
Chapter 3: How to create and care for a secure password to protect your account your email and instant messaging, as described below
Make your webmail remain private
The Internet is an open network where information can be sent in a readable form. If an email message hijacked before it gets to the recipient, it can be easily read.
And since the Internet is a global network that relies on a lot of computer traffic intermediaries as a director,
then a lot of people who had the opportunity to hijack your message in this way. Internet Service Provider (Internet Service Provider ISP)
is the first recipient of an email message that you send, on its way to the recipient.
Likewise with email being sent to you, ISP is the last stop before the message gets into your hands.
If you do not do certain steps, your message can be read or bothered at both time points, or in between.It's been a long time
we could secure the Internet connection between our computers with web sites that we visit.
This usually encountered when we have to enter a password or credit card information into the website.
The technology used is called the Secure Socket Layer encryption / SSL. We can know when we use SSL or not to look into the address bar of the browser we use.
All web addresses usually begins with the letters HTTP, as shown in the example below:
When you visit a secure site, its address will begin with HTTPS
Additional letter S at the end indicates that your computer has opened a secure connection (secure) to the website.
There can also see the symbol 'lock / padlock' in the address bar or in the status bar in the bottom of your browser window.
This is a sign that anyone who might want to monitor your Internet connection will not be able to 'eavesdrop' your communication with the website
In addition to protecting passwords and financial transactions you, this kind of encryption can also protect your webmail perfectly.
However, many webmail providers do not offer secure access, while others require you to activate it explicitly,
by selecting it in the settings section, or by typing in the HTTPS manually.
You should always make sure that your connection is secure before entering, reading or sending email messages.
Notice when your browser security flaw complained certificate when you try to access a secure webmail account.
This can mean that someone breaks the communication between your computer and the server to hijack your message.
Then, if you rely on webmail to exchange confidential information, it is important to ensure that you are using a browser that is reliable.
Consider installing Mozilla Firefox and its annexes relating to security.
Switching to a more secure email account
Only slight webmail providers offer SSL access to your email. For
example Yahoo and Hotmail, both provide a secure connection to
protect password when you sign in, but your messages are not sent and
received securely. Besides Yahoo, Hotmail and some providers of free
webmail service to include the IP address of the computer that you
use in all of the messages you send
In
contrast, Gmail accounts can be used entirely through a secure
connection, as long as you sign in to your account through
https://mail.google.com (using HTTPS), compared to
http://mail.google.com. In fact, you can now set the options so that
Gmail always use a secure connection. Unlike Yahoo or Hotmail, Gmail
does not tell you the IP address to the recipient. However, you are
advised not to rely on Google fully to maintain the confidentiality
of your email communications. Google to scan and record the contents
of messages of users for various purposes, and in the past they've
been given on demand governments that restrict digital freedom. For
more information about Google's privacy policy, see Further Reading
If
possible create new RiseUp email account by visiting
https://mail.riseup.net. RiseUp offers free email to activists around
the world and as best as possible to protect the information housed
in their servers. RiseUp has been believed since long ago as a
resource for those who need a secure email solution. Unlike Google,
RiseUp has a very strict policy with regard to users' privacy and
does not have a commercial interest in that one day may be contrary
to the policy. To create a new RiseUp account you need two 'invite
codes'. This code can be provided by someone who already has a RiseUp
account. If you have a print version of the booklet means that you
have received the 'invite codes' along with the book. If not, you
have to find two RiseUp users and ask him to send the code to you.
WEB
The
web site (English: website) is an interconnected web pages which are
generally located on the same servant contains a collection of
information provided by individuals, groups, or organizations. [1] A
web site is usually placed at least on a web server that can be
accessed over a network such as the Internet, or a local area network
(LAN) via the Internet addresses known as URLs. Combined all publicly
accessible sites on the Internet also referred to as the World Wide
Web, or better known by the acronym WWW. Although at least the home
page of the Internet site is generally accessible to the public
freely, in practice not all sites provide freedom for the public to
access it, some web sites require visitors to register as a member,
or even ask for payment to be aggota to be able to access content
contained the web site, such as sites that feature pornography, news
websites, e-mail services (e-mail), and others. These restrictions
generally done for reasons of security, respect for privacy, or for
certain commercial purposes.A web page is a file written as a plain
text file (plain text) are arranged and combined in such a way with
instructions based on HTML or XHTML, sometimes also inserted with a
little scripting language. The file is then translated by your Web
browser and displayed like a page on a computer monitor.The web pages
accessed by the user via the network communication protocol known as
HTTP, in addition to improving the safety and privacy aspects better,
the website can also implement a mechanism of accessing via HTTPS
protocol.
HISTORY
The inventor of the web site is Sir Timothy John "Tim" Berners-Lee, while web sites connected to the network first emerged in 1991.
The purpose of the team when designing a website is to facilitate exchange and update information on fellow investigators in which he worked.
On April 30, 1993, CERN (the place where Tim works)
announced that WWW can be used freely by the public.
A web site may be the work of an individual or individuals, or show
ownership of an organization, company. usually the discussion in a
website refers to a or some particular topic or purpose. A web site
may contain links that connect to other web sites, demkian also with
other web sites. This sometimes makes the difference between a
website that is created by the individual or individuals with web
sites created by business organizations to be not so clear.
They
are usually placed on a web server. A web server is generally
equipped with a device-specific software to handle the domain name
settings, as well as handle the service on the HTTP protocol called
HTTP Server (English: HTTP Server) such as the Apache HTTP Server, or
Internet Information Services (IIS).
DESCRIPTION
To be able to communicate with all computers connected to the Internet, use a communication protocol that uses TCP / IP (Transmission Control Protocol / Internet Protocol).
Every computer connected to the Internet has an address, such as 192.168.14.96. To obtain information or data on the Internet,
we can access it by typing a web address in the address bar.
Address of a site on the Internet called the domain name. So the domain name is a permanent address seen on the Internet site that is used to identify a site.
In other words, the Domain Name is the address used to find a site on the Internet.
Relation to the communication protocol TCP / IP, domain name can be likened to a phone book, we use a number to call someone.
for example when we mengekses www.wikipedia.com sites then the web browser Internet Explorer will contact an example IP 202.68.0.134.
General terms and the domain name is the URL (uniform resource locator), which is a means for determining the address that will be used to access the Internet.
The URL address is a special address for a particular file that can be accessed by Internet.
The URL address covers all other file types that can be accessed by the Internet, such as html files,
zip, rar, jpg, gif, and png.
INTRANET AND
EXTRANET
Definition
Intranet
intranet
is a private network (private network) that uses Internet protocol
(TCP / IP), to share confidential information about the company or
operating company to its employees. Sometimes, the term refers only
to intranet services visible, namely the company's internal Web
site.
To build an intranet, then the network should have some components that build the Internet, the Internet Protocol (TCP / IP, IP addresses, and other protocols), the client and the server. HTTP and other Internet protocols (FTP, POP3, SMTP or) is generally a component of a protocol used.
To build an intranet, then the network should have some components that build the Internet, the Internet Protocol (TCP / IP, IP addresses, and other protocols), the client and the server. HTTP and other Internet protocols (FTP, POP3, SMTP or) is generally a component of a protocol used.
Definition
Extranet
Extranet or Extranet
is a private network that uses Internet protocols and the public
telecommunication system to share some information securely business
or operations to the dealer (supplier), the seller (vendor), partner
(partner), customers and others.
Virtual
Private Network yang digunakan pada e-commerce
- Point to Point Protocol VPN
- Site to Site
- L2TP VPN
- SSL
- MPLS VPN
- Hybrid VPN
Merancang
strategi untuk menghadapi ancaman security
- Network Topology
- Security Information Management
- IDS/IPS
- Port Scanning
- Packet Fingerprinting
Jenis jenis
pembayaran dalam e-commerce
- Paypal
- Alertpay
- liberty Reserve
- watern union
- Cek
- Credit Card
- Transfer via bank
- Joint Account
- COD (Cash on delivery
- . Pulsa
- Cash
- Debit card
Tidak ada komentar:
Posting Komentar